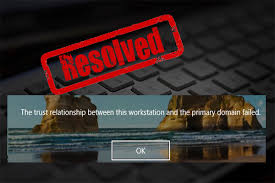
Understanding and Resolving: "The Trust Relationship Between This Workstation And The Primary Domain Failed"
Chính Sách Vận Chuyển Và Đổi Trả Hàng
Miễn phí vận chuyển mọi đơn hàng từ 500K
- Phí ship mặc trong nước 50K
- Thời gian nhận hàng 2-3 ngày trong tuần
- Giao hàng hỏa tốc trong 24h
- Hoàn trả hàng trong 30 ngày nếu không hài lòng
Mô tả sản phẩm
In the intricate ecosystem of Windows domain environments, a seamless connection between a workstation and its primary domain controller is paramount for security, resource access, and centralized management. When this connection falters, IT administrators and users alike are often met with a frustrating and disruptive error message: "The trust relationship between this workstation and the primary domain failed." This particular error is a clear indicator that the workstation is no longer securely recognized by the domain, leading to a cascade of problems from login failures to inability to access network resources or apply Group Policies. This comprehensive guide will delve into the underlying mechanics of this trust relationship, explore the myriad causes behind its failure, provide a systematic approach to diagnosis, offer detailed step-by-step solutions, and outline best practices for prevention, ensuring your domain environment remains robust and operational.
Understanding the Domain Trust Relationship
At its core, a domain trust relationship is a fundamental security mechanism within Active Directory (AD) that allows resources in one domain to be accessed by authenticated users and computers from another domain. In the context of "the trust relationship between this workstation and the primary domain failed," we are specifically referring to the secure channel established between a domain-joined computer (workstation or server) and its domain controller. This secure channel is crucial for authentication, authorization, and secure communication, enabling the workstation to participate fully in the domain.
How the Secure Channel and Machine Account Work
When a computer is joined to a Windows domain, Active Directory creates a computer object for it. This object has a unique machine account password. This password is automatically generated and securely stored by both the workstation and the domain controller. The secure channel is essentially a digitally signed and encrypted communication pathway established using this machine account password. Periodically, for security reasons, the domain controller initiates a change to this machine account password, and the workstation must update its copy accordingly. This ensures that the secure channel remains robust and prevents unauthorized entities from impersonating the workstation.
This dynamic, synchronized password mechanism is the bedrock of the trust relationship. It allows the workstation to authenticate itself to the domain controller, obtain Kerberos tickets for accessing domain resources, apply Group Policy objects (GPOs), and facilitate user logins. When the machine account password on the workstation no longer matches the one stored in Active Directory for that computer object, the secure channel breaks, and you encounter the message "the trust relationship between this workstation and the primary domain failed."
Why is a Healthy Trust Relationship Critical?
The integrity of this trust relationship is non-negotiable for several reasons:
- Authentication and Authorization: Without a valid trust, a workstation cannot authenticate itself to the domain. This means users logging onto that workstation using domain credentials will fail, as the workstation cannot verify their credentials against Active Directory.
- Resource Access: Access to network shares, printers, and other domain-based resources relies on the workstation's ability to communicate securely with the domain controllers and present valid Kerberos tickets.
- Group Policy Application: GPOs are the primary means of centralizing management and security settings within a domain. A broken trust means GPOs will not apply, leaving the workstation in a potentially non-compliant or insecure state.
- Security: The secure channel protects communication between the workstation and domain controllers, preventing eavesdropping or tampering. A broken trust compromises this security.
Common Causes of "The Trust Relationship Between This Workstation And The Primary Domain Failed"
While the immediate cause of "the trust relationship between this workstation and the primary domain failed" is always a mismatch in the machine account password, several scenarios can lead to this mismatch. Understanding these underlying causes is key to efficient troubleshooting.
1. Restoring from a Backup or Snapshot
One of the most frequent culprits, especially in virtualized environments, is restoring a workstation from an old backup or snapshot. If the backup was taken before the machine account password was last changed by the domain controller, the restored workstation will have an outdated password. When it attempts to communicate with the domain, its password won't match the one on the domain controller, leading to a trust failure.
2. Cloning Virtual Machines Without Sysprep
When cloning a virtual machine (VM) that was already joined to a domain without using the System Preparation Tool (Sysprep), the cloned VM will inherit the original VM's Security Identifier (SID) and machine account. If both the original and cloned VMs are on the network simultaneously, or if the original VM's machine account password changes, the cloned VM will quickly run into trust issues due as its machine account is a duplicate or becomes outdated.
3. Workstation Offline for an Extended Period
If a workstation remains disconnected from the network (e.g., a laptop stored away) for longer than the machine account password change interval (default is 30 days), it will miss the automatic password updates initiated by the domain controller. Upon reconnecting, its stored password will be out of sync.
4. Time Synchronization Issues
Kerberos authentication, which is central to Active Directory, is highly sensitive to time differences. If the workstation's clock is significantly out of sync with the domain controller's clock (typically more than 5 minutes), Kerberos tickets will be deemed invalid, preventing successful authentication and manifesting as a trust issue.
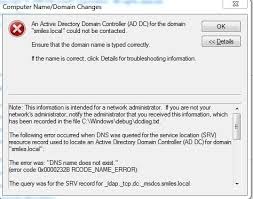
5. Network Connectivity and DNS Resolution Problems
A workstation must be able to resolve domain controller names to their IP addresses and communicate with them. If DNS settings are incorrect (e.g., pointing to an external DNS server instead of the domain controller), or if there are network connectivity issues (firewall, cabling, IP configuration), the workstation cannot establish or maintain its secure channel, leading to a trust failure.
6. Corrupted Machine Account
In rare cases, the computer object in Active Directory itself might become corrupted, or its attributes (including the machine account password hash) might be altered incorrectly. This can also happen if the computer object was accidentally deleted and then recreated, which often creates a new machine account and invalidates the old one.
7. Manual Computer Name Changes
If a computer's name is changed while it is joined to the domain, without following the proper domain-integrated renaming procedure, it can break the machine account's association, leading to a trust relationship error.
Diagnosing the Trust Relationship Failure
Effective diagnosis is crucial to pinpoint the exact cause and apply the correct solution. Before attempting any fixes for "the trust relationship between this workstation and the primary domain failed," gather as much information as possible.
Initial Checks:
- Network Connectivity:
- Ping the domain controller by its IP address and then by its Fully Qualified Domain Name (FQDN).
- Verify the workstation's IP configuration (IP address, subnet mask, default gateway).
- Ensure the primary DNS server listed on the workstation's network adapter is a domain controller.
- Time Synchronization:
- Compare the workstation's date and time with that of a domain controller. Use
w32tm /query /sourceto see the time source. - Manually synchronize if necessary:
w32tm /resync.
- Compare the workstation's date and time with that of a domain controller. Use
- Event Viewer:
- Open Event Viewer (
eventvwr.msc) and navigate toWindows Logs > System. - Look for errors from sources like Netlogon (Event ID 5719, 5722), Kerberos, or DNS Client. These provide specific clues about the nature of the trust issue.
- Open Event Viewer (
Using Command-Line Tools:
nltest /sc_query: <DomainName>: This command is invaluable for checking the secure channel status. A healthy status will show "Status = NERR_Success". If it's broken, it will report an error like "NERR_DCNotFound" or "Status = 1789 0x6fd ERROR_TRUSTED_RELATIONSHIP_FAILURE".nltest /sc_verify:<DomainName>: Similar to/sc_query, but also attempts to verify the secure channel.set logongroup: Displays the current logon server for the workstation. If it's not a domain controller, this indicates a problem.ipconfig /all: Confirm DNS server configuration and other network details.nslookup <DomainName>: Verify DNS resolution for your domain.
Step-by-Step Solutions to Resolve "The Trust Relationship Between This Workstation And The Primary Domain Failed"
Once you've diagnosed the problem, you can proceed with solutions. The preferred method for resolving "the trust relationship between this workstation and the primary domain failed" is to reset the machine account password, as it's less disruptive than rejoining the domain.
Method 1: Resetting the Machine Account Password (Preferred Approach)
This method attempts to synchronize the workstation's machine account password with Active Directory without unjoining and rejoining the domain. You can perform this from the workstation itself (if you can log in with a local administrator account) or from a domain controller.
A. Using Netdom Command (from the Workstation - Local Admin required)
This is often the quickest and most effective way if you can log into the workstation with a local administrator account.
- Log in to the affected workstation using a local administrator account.
- Open an elevated Command Prompt (Run as administrator).
- Execute the following command, replacing
<WorkstationName>with the workstation's name and<DomainName>with your domain's NetBIOS name:netdom.exe resetpwd /s:<DomainControllerName> /ud:<DomainAdminAccount> /pd:*Example:
netdom.exe resetpwd /s:DC01 /ud:CONTOSO\Administrator /pd:*You will be prompted to enter the password for the domain administrator account. This command attempts to reset the computer account password on the domain controller, and then updates the workstation's local password to match.
- If successful, you should see a message confirming the command completed successfully.
- Restart the workstation.
- Attempt to log in with a domain account to verify the trust relationship is restored.
Note: If you don't have local admin access on the workstation, you'll need to use Method 1B.
B. Resetting from Active Directory Users and Computers (from a Domain Controller)
This method resets the computer object's password in Active Directory. The workstation will then automatically pick up this new password on its next secure channel establishment attempt.
- Log in to a domain controller or a computer with RSAT (Remote Server Administration Tools) installed, using a domain administrator account.
- Open Active Directory Users and Computers (
dsa.msc). - Navigate to the Computers container (or the Organizational Unit where the workstation's computer object resides).
- Right-click on the affected workstation's computer object.
- Select Reset Account....
- Confirm the action when prompted. This effectively resets the machine account password in Active Directory.
- Go to the affected workstation. If it's already running, open an elevated Command Prompt and run:
nltest /sc_verify:<DomainName>This command forces the workstation to attempt to re-establish the secure channel with the new password. If this fails, a restart of the workstation is usually sufficient.
- Restart the workstation.
- Attempt to log in with a domain account to confirm the trust relationship is fixed.
Method 2: Rejoining the Domain (More Disruptive, but Highly Effective)
If resetting the account password fails, or if you prefer a more definitive solution, rejoining the domain is a reliable option. This involves removing the workstation from the domain and then adding it back.
- Log in to the affected workstation using a local administrator account. This is crucial as domain accounts will not work.
- Open System Properties (
sysdm.cpl). - Go to the Computer Name tab.
- Click Change....
- Under "Member of", select Workgroup and enter a temporary workgroup name (e.g., WORKGROUP).
- Click OK. You will be prompted to provide domain administrator credentials to remove the computer from the domain. Enter the credentials of a domain admin.
- Restart the workstation when prompted.
- After the restart, log in again with the local administrator account.
- Go back to System Properties > Computer Name > Change....
- Under "Member of", select Domain and enter your domain's FQDN (e.g.,
contoso.com). - Click OK. You will be prompted for domain administrator credentials to join the domain. Enter the credentials of a domain admin.
- Restart the workstation when prompted.
- After the restart, attempt to log in with a domain account to confirm that "the trust relationship between this workstation and the primary domain failed" error is resolved.
Important Note: Rejoining the domain will create a new computer object in Active Directory if the old one was deleted. If the old object still exists, the rejoin process will reuse it. However, if any specific permissions were set on the original computer object in AD, these might need to be re-applied.
Method 3: Advanced Troubleshooting Steps
If the above methods don't work, consider these more advanced steps:
- Clear DNS Cache: On the workstation, open an elevated Command Prompt and run
ipconfig /flushdns. - Verify Computer Object in Active Directory: Ensure the workstation's computer object exists in AD and is not disabled. Check its properties for any anomalies.
- Check for Duplicate Computer Names/SIDs: In rare cases, a duplicate computer name or SID might be causing conflicts. Tools like
AD ExplorerorPsGetSidcan help investigate this, though it's typically handled by Sysprep. - Force Replication (for multiple DCs): If you have multiple domain controllers, ensure the computer object's status has replicated across all DCs. You can use
repadmin /syncallfrom a domain controller. - Check Domain Controller Health: Ensure the domain controllers are healthy, reachable, and their Netlogon service is running. Use
dcdiagon the DCs.
Preventing Future Trust Relationship Failures
Proactive measures are always better than reactive fixes. To minimize the chances of encountering "the trust relationship between this workstation and the primary domain failed" error in the future, consider the following best practices:
- Proper VM Cloning: Always use Sysprep (System Preparation Tool) when creating gold images or cloning virtual machines that will be joined to a domain. Sysprep generalizes the image, removing unique SIDs and machine account information, forcing the new VM to generate its own upon first boot.
- Regular Connectivity: Ensure laptops and other mobile devices are regularly connected to the corporate network to allow their machine account passwords to synchronize with domain controllers.
- Accurate Time Synchronization: Implement a robust time synchronization strategy using Group Policy to ensure all domain-joined computers synchronize their time with authoritative domain controllers (which should synchronize with reliable external NTP sources).
- Monitor Event Logs: Regularly review system logs on workstations and domain controllers for Netlogon errors (Event ID 5719, 5722) or Kerberos errors. Early detection can prevent widespread issues.
- Careful Backup and Restore: Be aware that restoring system state backups or snapshots can break trust relationships if they are too old. Plan your backup strategy accordingly, especially for domain-joined machines.
- Active Directory Maintenance: Avoid manually deleting and recreating computer objects in Active Directory unless absolutely necessary and with full understanding of the implications. Use the "Reset Account" feature where appropriate.
- Network Health: Maintain a healthy and reliable network infrastructure with correctly configured DNS servers.
Impact on Users and Business Operations
When "the trust relationship between this workstation and the primary domain failed" error occurs, the impact can be significant, ranging from individual user frustration to considerable business disruption:
- Inability to Log In: The most immediate and noticeable impact is that users cannot log into the workstation using their domain credentials. This means they cannot access their profiles, files, or applications.
- Loss of Network Resource Access: Even if a local login is possible, the workstation loses its ability to authenticate with the domain, blocking access to shared folders, network printers, and other domain-dependent resources.
- Group Policy Ineffectiveness: The workstation will stop receiving and applying Group Policy updates, potentially leaving it vulnerable to security threats or out of compliance with organizational standards.
- Productivity Loss: Users become unproductive, and IT staff must divert resources to troubleshoot and resolve the issue, leading to downtime and increased operational costs.
- Security Vulnerabilities: A workstation that cannot securely communicate with its domain controller is a security concern, as it might not be enforcing critical security policies.
Conclusion
The error message "the trust relationship between this workstation and the primary domain failed" is a common yet critical issue in Windows domain environments, indicating a breakdown in the secure communication channel between a computer and its domain controller. While seemingly complex, its root cause often boils down to a mismatch in the machine account password, triggered by various scenarios like outdated backups, improper VM cloning, or prolonged disconnections. By understanding the fundamental role of the trust relationship, systematically diagnosing the problem through Event Viewer and command-line tools, and applying the appropriate solutions—primarily resetting the machine account password or rejoining the domain—IT professionals can efficiently restore connectivity and functionality.
Furthermore, implementing proactive measures such as diligent Sysprep usage for VM cloning, ensuring regular network connectivity for all devices, maintaining accurate time synchronization, and vigilant monitoring of Event Logs are indispensable for preventing these trust failures. A healthy trust relationship is the backbone of a secure, manageable, and productive Active Directory environment, and mastering its intricacies is essential for any system administrator.